Preventing Common Attacks Security Guideline
Product Engineering, AINQA Healthcare
March 2022
1.Purpose of this Document
The purpose of the document is to provide high-level guidelines for securing AINQA’s cutting-edge applications from common attacks. The document will become the basis of developing and securing applications that AINQA provides to clients. The scope will be for internal and external applications deployed. As for the internal applications, this mainly involve various environment such as UAT / SIT / STAGING and production. This document also can be used against vendor or partner products ensuring their products are comply to AINQA product security guidelines.
The target audience will be mainly from development team members of AINQA that develop applications in day-to-day basis. It is also targeted at solution architecture level employees that design applications for AINQA. It is also for general AINQA employees to know the high-level details on the applications security that practiced at AINQA so that they will be better informed of the AINQA products from the security perspective.
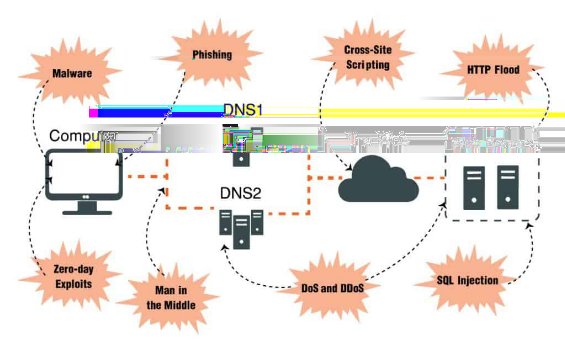
Figure 1: Common Types of Cyber Attacks
2. Type of Attacks / Vulnerabilities
This document will be a live document exploring the key and popular vulnerabilities among the adversaries. Brief description is provided of each vulnerability and remediation activities are recommended with the target person responsible for. If needed relevant step-by-step guidance URL is provided for the developers to address the vulnerabilities.
2.1 Malware
“Malware” refers to various forms of harmful software, such as viruses and ransomware. Once malware is in a computer, it can wreak all sorts of havoc, from taking control of a machine, to monitoring actions and keystrokes, to silently sending all sorts of confidential data from a computer or network to the attacker's home base.
Malware is a piece of code that crafted to harm a computer or server. It could be in the form of virus or ransomware. Once infected with malware, it can wreak all kinds of havoc from taking control of a machine, sending all sorts of confidential data from a computer or network to attackers’ computer, to monitoring actions and keystrokes performed and many more.
Once a system is fully compromised the attacker can use it for various gains from using it for DoS / DDoS attacks, demanding payment (ransomware) or worst-case scenario wiping out the entire system.
Remediation
1) User Education (end users)
Training users on best practices for avoiding malware (i.e., don’t download and run unknown software, don’t blindly insert “found media” into computer), as well as how to identify potential malware (i.e. phishing emails, unexpected applications/processes running on a system). Periodic, unannounced exercises, such as intentional phishing campaigns, can help keep users aware and observant. It is believed that only about 3% of Malware is able to exploit a technical flaw. The remaining, 97% relies on tricking humans through social engineering to gain easier access into the network. Therefore, the education aspect is the most important in addressing the malware attacks.
Responsibilities: IT Support Manager / Information Security Manager
1) Tools
Using reputable A/V solutions to detect and remove any existing malware on system as well monitor for and mitigate potential malware installation or activities. It is also more important to keep it up to date with the vendors latest definitions or signatures.
Responsibilities: IT Support Manager
1) Securing Network
Using proven technologies to prevent malware reaching the organization’s network. This involves having firewall, IPS, IDS and remote access only through VPN which will help minimizing the attack 'surface' of AINQA.
Responsibilities: Infra Service Providers / Network Engineers / Information Security Manager
1) Application Auditing
Scanning applications regularly for vulnerabilities (i.e., software with known bugs, server/service/application misconfiguration) and to detect if known malware has been installed can keep AINQA secure, protect employees, and protect customers and visitors for public-facing AINQA sites.
Responsibilities: Security Engineer, DevOps, Service Providers
2.2 Phishing
Phishing happens when attackers attempt to trick users into doing 'the wrong thing', such as clicking a bad link that will download malware or direct them to a vulnerable website. Phishing can be conducted via a text message, social media, or by phone, but the term 'phishing' is mainly used to describe attacks that arrive by email.
Remediation
- Filter or block incoming phishing emails
- Getting users to report any suspected phishing emails by means of established process
- Educate users through awareness programs
- Prevent users accidentally installing malware from a phishing email, by limiting administrator accounts to those who need those privileges.
- Prevent attackers from using known vulnerabilities by only using supported software and devices and with latest patches
Responsibilities: IT Support / End Users
2.3 Man in the Middle
Man-in-the-middle attacks (MITM) are a common type of cybersecurity attack that allows attackers to eavesdrop on the communication between two targets. The attack takes place in between two legitimately communicating hosts, allowing the attacker to “listen” to a conversation they should normally not be able to listen to.
Remediations
- Add a VPN to encrypt traffic between end-points and the VPN server (either on the enterprise network or on the internet).
- Use end-to-end encryption for your emails, chat, and video communication (Zoom, Teams, etc.)
- Use multi-factor authentication wherever available
- Employ DNS over HTTPS, which is a new technology that protects you from DNS hijacking by encrypting your DNS requests
- Session management is handled properly considering various techniques in manipulating it. i.e., tokens renewed / reauthenticated / authorized
Responsibilities: Developers / Solution Architects
2.4 DoS and DDoS
A distributed / denial of service (DDoS) attack is a malicious attempt to make an online service unavailable to users, usually by temporarily interrupting or suspending the services of its hosting server. There are few commonly used DoS / DDoS attack using UDP Flood, ICMP (Ping) Flood, SYN Flood, Ping of Death, NTP amplification and HTTP Flood.
The symptoms of DoS /DDoS are:
- Exponential, unexpected rise in traffic at a single endpoint/server.
- A server starts repeatedly crashing for no reason.
- Huge amounts of traffic coming from clients with same or similar characteristics.
The following sections briefly discuss numerous methods used in DoS and DDoS attacks.
2.4.1 Application Layer Attacks

Figure 2: Application Layer Attack using DOS
In an application layer attack occurs when a hacker uses different bots/machines to repeatedly request the same resource from the server, eventually overwhelming it and therefore the server will crash or rebooted. This will disrupt services to genuine requests.
2.4.2 Protocol Attacks

Figure 3: Protocol Attacks
Protocol attacks look to exhaust resources of a server or those of its networking systems like firewalls, routing engines, or load-balancers. An example of a protocol attack is the SYN flood attack. It exploits part of the normal TCP three-way handshake to consume resources on the targeted server and render it unresponsive.
Essentially, with SYN flood DDoS, the offender sends TCP connection requests faster than the targeted machine can process them, causing network saturation.
2.4.3 Volumetric Attacks

Figure 4: Volumetric Attacks
Volumetric distributed denial of service (DDoS) attacks are distinct from the other two types of DDoS attacks—protocol DDoS attacks and application layer DDoS attacks—because they’re based on brute force techniques that flood the target with data packets to consume bandwidth and resources. The other two attack types generally use considerably less bandwidth and are also more focused on specific aspects of their targets such a particular protocol or a service.
Remediation
- Ensuring the network devices such IPS / IDS and F/W recognize the patterns of DoS / DDoS attacks and block the traffic from origination servers, meaning only filtered traffic reaches AINQA developed or partner applications.
- Ensuring unused ports / services are closed, i.e., NTP
- Real-time packet analysis, a popular method used by various tools i.e., IDS / IPS by discarding malicious traffics
- DDoS defense system (DDS) is dedicated tools that detect legitimate-looking content with malicious content.
- Web application firewall, a great tool to mitigate application layer DoS attacks.
- Rate limiting which will limit the number of request a server can entertain over a certain period of time.
Responsibilities: Network Engineers / Service Providers
2.5 Cross Site Scripting (XSS)
Cross-site scripting works by manipulating a vulnerable web site so that it returns malicious JavaScript to users. When the malicious code executes inside a victim's browser, the attacker can fully compromise their interaction with the application.

Figure 5: Cross Site Scripting
Remediation
- Filter input on arrival or validating the inputs particularly watching out for tags in user-supplied input
- Encode data on output. At the point where user-controllable data is output in HTTP responses, encode the output to prevent it from being interpreted as active content. Depending on the output context, this might require applying combinations of HTML, URL, JavaScript, and CSS encoding.
- Use appropriate response headers. To prevent XSS in HTTP responses that aren't intended to contain any HTML or JavaScript, we can use the Content-Type and X-Content-Type-Options headers to ensure that browsers interpret the responses in the way we intend.
- Content Security Policy. Using Content Security Policy (CSP) to reduce the severity of any XSS vulnerabilities that still occur.
- Use Tokens / advise logout / automatically logout after certain period of time
Responsibilities: Developers
2.6 HTTP Flood
An HTTP or HTTPS flood is a type of Distributed Denial of Service (DDoS) attack in which at attempt is made to overload a web server or application with a flood of HTTP/S requests. Such DDoS attacks on the application layer (Layer 7) are among the most common forms of attack today.

Figure 6: HTTP Flood Attack
In an HTTP flood attack attackers flood a web server with HTTP requests that specifically request pages with large loading volumes. This ultimately causes the server to overload and it is no longer able to process legitimate requests. As a result, the website or web application is no longer accessible for users. Cybercriminals often employ botnets for such attacks to maximize the efficiency and impact of their attacks.
The HTTP provides several methods for exchanging data between a web browser and a website. By far the most commonly used are HTTP GET and HTTP POST. A GET request fetches information from the server without changing any data on it. With the POST method, data is sent to and processed on the server, such as content from a web form. HTTP flood attacks typically take advantage of these two HTTP methods.
Remediation:
Once an attack traffic is identified through network devices, the requests associated with it can be blocked or discarded. The Requests classified as illegitimate can regain their status as legitimate requests by resolving a CAPTCHA. After being successfully verified, they are forwarded to the web server and responded to. Security at OSI Layer 7 needed because network/transport layers won’t be able to differentiate between HTTP GET and valid request
Responsibilities: Network Engineers / Service Providers
2.7 SQL Injection
SQL Injection (SQLi) is a type of an injection attack that makes it possible to execute malicious SQL statements. These statements control a database server behind a web application. Attackers can use SQL Injection vulnerabilities to bypass application security measures. They can go around authentication and authorization of a web page or web application and retrieve the content of the entire SQL database.
Remediation
SQL injection can be prevented by using parameterized queries (also known as prepared statements) instead of string concatenation within the query.
Responsibilities: Developers
2.8 Zero Day Exploits
The “Zero-day” definition encompasses all unknown or new attacks, exploiting vulnerabilities for which no patch has yet been released. The term is well-known amongst the members of the hacker community, where the practice of trading zero-day vulnerabilities has become a popular activity. To ensure AINQA does not fall into zero-day attacks, our processes have to be in place that addresses various surface attacks from network to computers to development practices.
The emphasize should be given to the AINQA development team educating them on the various application vulnerabilities and how this can be addressed by practicing secure coding through SSDLC, making it as a culture amongst the developers